Shield Your Web Assets
CyberShield is an AI-powered enterprise security platform with real-time detection, cloud protection, and automated compliance.
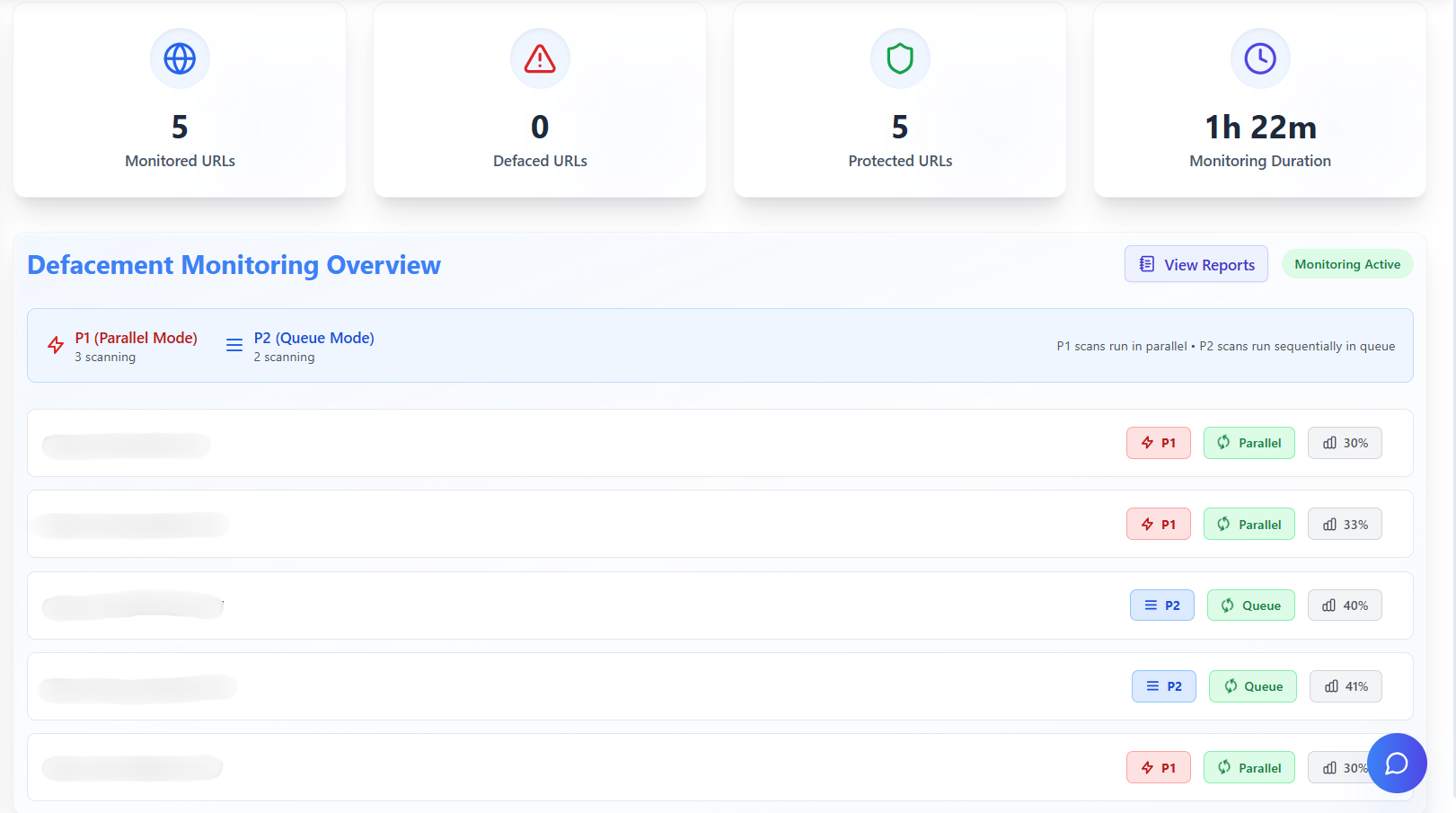
Your Website and Mobile App is Under Attack Every Minute
Modern enterprises face unprecedented web security challenges. Traditional firewalls are no longer enough.
Critical Warning: Traditional tools miss 60% of vulnerabilities in authenticated apps.
One platform for monitoring and protection
Explore our comprehensive security modules
Defacement Detection
AI-powered visual analysis catches what others miss. Real-time integrity checks ensure your digital face remains spotless.
Downtime Monitoring
Instant alerts for outages and performance degradation. Monitor your uptime from multiple global locations 24/7.
Misconfiguration Detection
Identify security gaps in your server headers, SSL configurations, and exposed sensitive files before attackers exploit them.
Vulnerability Scanner
Deep dive into your application logic. Authenticated scanning for OWASP Top 10, CVEs, and business logic flaws.
Port Scanner
Discover exposed services and open ports on your network. Prevent unauthorized access points and mitigate attack surface.
Mobile App Scanner
Comprehensive static and dynamic analysis for Android (APK) and iOS (IPA) applications to secure your mobile presence.
Why Global Enterprises Choose
CyberShieldPro
Built for mission-critical security. Validated by the best.
Military-Grade Validation
- Designed and deployed by MoD
- Protects sensitive and critical digital assets
- Comprehensively tested and validated in an operational environment
AI-Powered Intelligence
- 98% Accuracy in Defacement Detection
- Zero-day threat prediction models
- On-premise AI (Data never leaves)
India-First Compliance
- CERT-In 6-hour automated reporting
- Full Data Residency Compliance
- Native Hindi Language Support
Trusted by Industry Leaders
Securing the next generation of digital infrastructure






Ready to Secure
Your Digital Assets
Join leading enterprises using CyberShield for advanced threat protection and real-time monitoring.